This post covers installation of Oracle Identity Manager (OIM) connector to provision or reconcile users to/from Oracle Internet Directory (OID). There is another way to integrate OIM 11g with OID 11g using Oracle Virtual Directory (OVD) which is LDAP Sync .
This post is for OIM-OID integration using pre-built connector and assumes that
- Oracle Internet Directory is already installed, for OID 11g installation click here.
- Oracle Identity Manager is already installed, for OIM 11g installation click here
.
OIM Connector for OID Key Points
- Current OIM connector version for OID is 9.0.4.14
- You can use OIM-OID connector version 9.0.4.12 to integrate OIM 9.X/11g with OID 10g/11g
- This post uses OID superuser “cn=orcladmin” to connect from OIM to OID (It is recommended to create user in OID, dedicated to be used by OIM-OID connector)
.
OIM-OID connector installation/configuration
1. Download OIM-OID connector from here
2. Download LDAP-1_2_4.zip from here (Click on “Download JNDI 1.2.1” and then click on ldap-1_2_4.zip) extract LDAP-1_2_4.zip and copy ldap.jar, ldapbp.jar (this is under lib directory) and copy it to $ORACLE_HOME/server/ThirdParty (on OIM Server)
3. Install OIM-OID connector
3.1 Copy OIM/OID connector software (OID_904120.zip) to $ORACLE_HOME/ server/ ConnectorDefaultDirectory (on OIM Server)
3.2 Unzip OID_904120.zip
3.3Login to OIM Administrator URL (http://server:14000/oim - xelsysadm / xelsysadm_password)
3.4 Click on Advanced tab (This is OIM Advanced Administration Console)
.
.
3.5 Click on Install Connector under System Management
.
.
3.6 From Connector List drop down select “Oracle Internet Directory 9.0.4.12” and click Load and then click on Continue
.
.
3.8 On successful connector installation, message indicating successful installation is displayed. In my case installation failed at compilation
“DOBJ.EVT_INTERNAL_ERROR Adapter Compilation Failure Bulk Exception”
.
.
.
Check logs in $MW_HOME/ user_projects/ domain/ base_domain/ servers/ oim_server1/ logs
____________
internal error. : /tmp/oracle/oim/adapters/adpOIDCREATEUSER.java (Too many open files)>
/tmp/oracle/oim/adapters/adpOIDADDUSERTOROLE.java (Too many open files)
java.io.FileNotFoundException: /tmp/oracle/oim/adapters/adpOIDADDUSERTOROLE.java (Too many open files)
at java.io.FileOutputStream.open(Native Method)
at java.io.FileOutputStream.
at java.io.FileOutputStream.
Fix : Increase number of open file by updating /etc/security/limits.conf
.
3.9 Run Oracle Identity Manager PurgeCache utility to load the server cache with content from the connector resource bundle in order to view the list of prerequisites
set WL_HOME
ORACLE_HOME/server/bin/purgeCache.sh All
When prompted for
[Enter the admin username:] entter xelsysadm
[Enter the admin username:] entter xelsysadm
[Enter the service URL:] t3://server:14000
Note: Ensure that WebLogic Full Client jar file is created under $WL_HOME/server/lib/wlfullclient.jar , check here
3.10 Configure IT resource
3.10.1Login to OIM Administrator URL (http://server:14000/oim - xelsysadm/xelsysadm_password) and click on Advanced tab on top right menu bar
3.10.2 Click on “Manage IT Resource” under Configuration
.
.
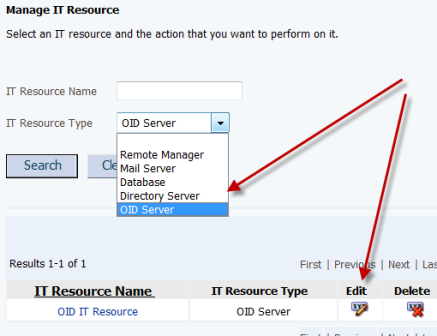
3.10.3 In the IT Resource Type field on the Manage IT Resource page, select OID Server and then click Search. Click the edit icon for the IT resource.
.
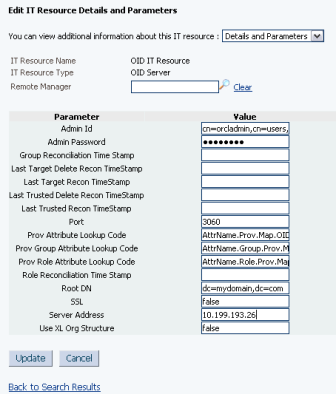
3.10.4 Specify values for the parameters of the IT resource.
Admin ID: DN value of the user who has administrator rights on the Oracle Internet Directory server (cn=orcladmin,cn=users,dc=mydomain,dc=com)
Admin Password : Password of user mentioned in Admin ID
Root DN: OID Domain (also called Realm)
Port : OID Port (default port for OID 11g is 3060 and for OID 10G 389 )
Server: OID Server
.
.
4. Perform first time reconciliation
First-time or full reconciliation involves reconciling all existing user records from the target system (OID) into Oracle Identity Manager (OIM)
4.1Perform lookup field synchronization (Run following tasks - Organization Lookup Reconciliation, Role Lookup Reconciliation, Group Lookup Reconciliation)
4.1.1From OIM Administration console, click on “Advanced” under “System Management” click on “Search Scduled Jobs” and search for “OID Organization Lookup Reconciliation”, Click on “Run Now”
Repeat this for “OID Role Lookup Reconciliation” & “OID Group Lookup Reconciliation”
4.2 Perform user reconciliation
4.2.1From OIM Administration console, click on “Advanced” under “System Management” click on “Search Scheduled Jobs” and search for “OID User Target Recon Task“, click on “Run Now”
If you get error like
______
Exception java.lang.NoClassDefFoundError: com/sun/jndi/ldap
Message /ctl/PagedResultsControl
_______
Enure that you have ldapbp.jar & ldap.jaris in $ORACLE_HOME/server/ThirdParty
5. Test Provisioning Operation using link here
.
References